SBOM
Produce SBOMs From Binaries to Self-Attest as a Software Vendor or Verify Third-Party Software as a Consumer.
Produce SBOMs From Binaries
Comply with Regulatory and Customer Requirements
Concerns over the security of software delivered to corporations and the US Government have steadily grown. The supply chain attacks on SolarWinds and the Log4j exploit have prompted action.
Those attacks provided backdoor access to hundreds of private sector entities and at least 9 Federal Agencies, including the Departments of Defense, Commerce, Energy, Justice, Homeland Security, State, Treasury, and the National Institute of Health.
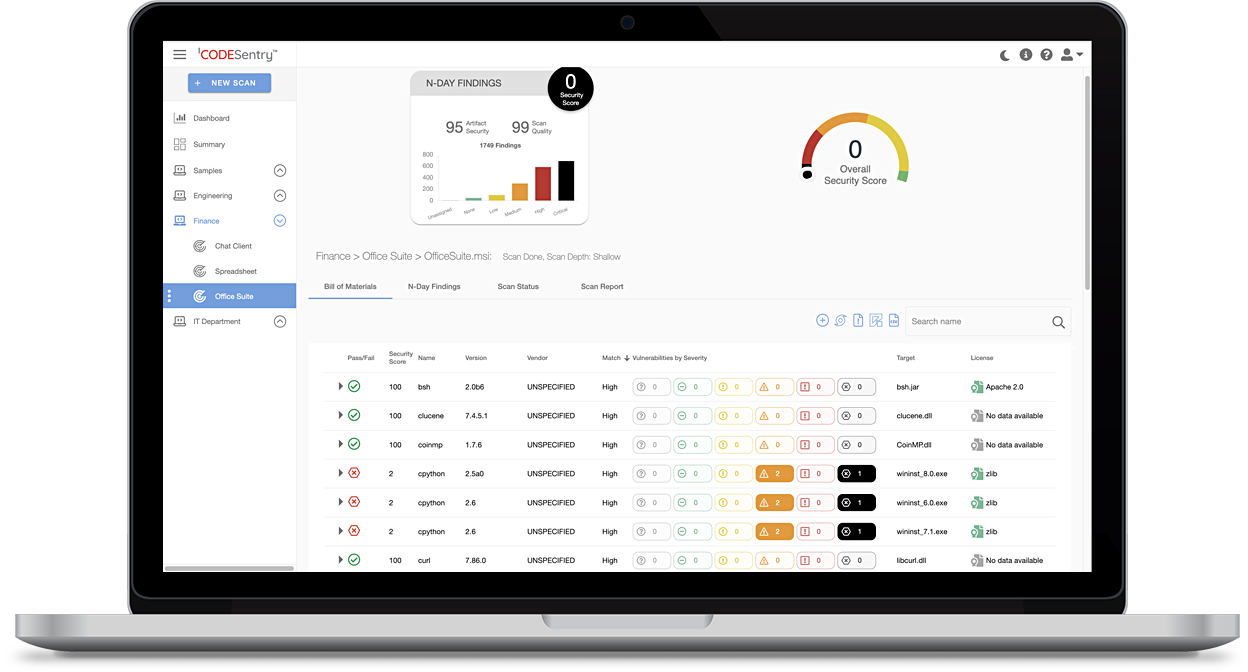
Generate Vendor Release Documentation
Key Artifact for Engineering
SBOMs are a formal, human, and machine-readable inventory of software components, dependencies, and their vulnerabilities and licenses. They’re designed to track the details and supply chain relationships of software components, their dependencies, and their hierarchal relationships.
The purpose of SBOMs is to provide transparency into the components that make up their software so that vulnerabilities can be tracked and fixed and IP protected from licensing conflicts.
Fulfill Security and Customer Requirements for SBOMs
Best Practice and Regulatory Requirements
Third party components present the dominant attack surface in software, with well over half of the average application comprised of open source and other third party components. An SBOM provides security, risk, and compliance personnel with the information needed to secure this portion of the code base.
While internal stakeholders are the primary audience for an SBOM today, expect that to change. Corporate customers recognize the risk to their systems from insecure vendor applications.


Meet Regulatory Requirements
Federal SBOM Requirements
The federal government are requesting SBOMs with any software they purchase. Software in this definition includes any application Software or Products that contain software (i.e., firmware, operating systems, applications services as well as products containing software).
Our Customers






























































































































































































































Case Studies
Learn how customers gain value using CodeSecure’s solutions via case studies in medical, aerospace, tech, and more.
Browse all Case Studies-
eLeapPower
Learn MoreThe Challenge: Finding a scalable Static Application Security Testing (SAST) solution to support a lean team of experienced software engineers as they innovate new solutions while adhering to strict software cybersecurity and functional safety requirements in the auto industry.
-
LeddarTech
Learn MoreThe Challenge: To build the LeddarVision software platform according to automotive industry requirements, starting in the design stage, and integrate checks in the development workflow in compliance with ISO26262 functional safety requirements for road vehicles, MISRA C, MISRA C++ and AUTOSAR C++ coding standards and security requirements such as CERT C++.
-
Telit
Learn MoreCodeSecure Helps Telit Deliver Safety Faster. Telit is a global leader in cellular-based M2M and Internet of Things (IoT) solutions that have been connecting the world from the inside out for nearly 20 years.
-
Piper
Learn MoreTransportation – CodeSecure Helps Optimize Smart Sensors and Technologies to Increase Transportation Throughput.
-
Petroleum Experts
Learn MoreIndustrial – CodeSecure Helps Deliver High Quality, Safe, Secure Software and Ensure Customer Satisfaction.
-
NASA-White Sands: The Benefit of Static Analysis
Learn MoreAerospace – CodeSecure Contributes to NASA Study Exploring the Benefits of Static Analysis.
Related Resources
View all blog posts-
Who’s Responsible for Securing Containers that Developers Work In?
Read More -
Software Engineering Certifications Rolling Out Soon
Read More -
Certifying Critical OT System Engineers
Read More -
Getting Physical with Cybersecurity
Read More -
Will the FDA Start Banning Chinese-Made Medical Devices?
Read More -
Lessons on C and C++ Secure Coding Practices with Tanya Janca
Read More
Book a Demo
We’re ready to help you integrate SAST and BCA security into your DevSecOps flow. Get a personally guided tour of our solution offerings to ensure you are receiving the right solution for your development team.
book now





