Understanding the Critical Role of SAST in Modern Software Security
Static Application Security Testing (SAST) has become an essential component in modern software development. As organizations race to deliver software faster than ever, security cannot be an afterthought.
Application vulnerabilities now represent the number one attack vector for malicious actors. Detecting these vulnerabilities early isn’t just good practice, it’s crucial for protecting your business and customers.
The financial implications are clear: fixing security issues during development costs a fraction of remediation after deployment. SAST brings security directly into your development workflow, allowing teams to build secure code from the start.
How SAST Works: Understanding the Technical Foundation
Source Code Analysis Methodology
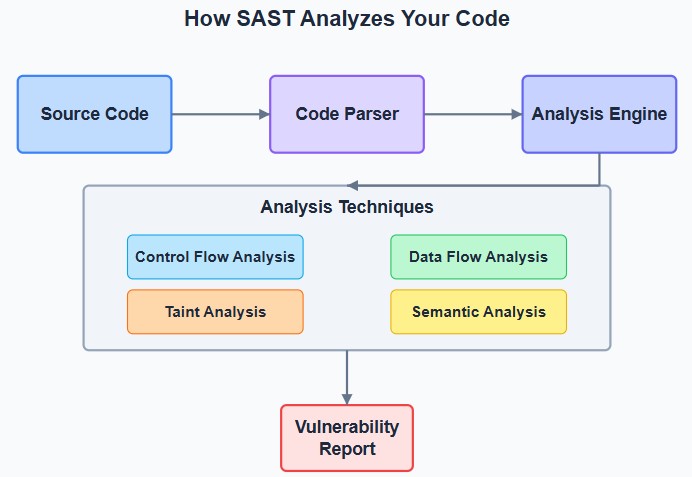
SAST analyzes your source code or binaries without executing them, searching for potential security vulnerabilities and quality issues. It’s like having a security expert reviewing every line of code, only faster and more thorough.
Unlike dynamic testing methods, SAST examines code from the inside out. It identifies vulnerabilities by analyzing code structure, data flow, and control flow to find issues before they make it into production.
Modern SAST tools employ sophisticated algorithms to understand code context, detect complex vulnerability patterns, and minimize false positives that can drain developer resources.
Beneath the Hood
SAST engines typically use techniques such as:
- Taint analysis: Tracking untrusted data through the application
- Control flow analysis: Examining all possible execution paths
- Data flow analysis: Following how variables are used throughout the code
- Semantic analysis: Understanding code behavior and context
These techniques work together to provide comprehensive coverage of potential vulnerabilities across your codebase.
The Business Case for SAST: ROI and Organizational Benefits
Early Detection and Cost Reduction Benefits
Implementing SAST early in development delivers substantial benefits:
- Cost efficiency: Fixing vulnerabilities during development costs up to 100x less than post-release remediation.
- Accelerated development: Issues identified early prevent costly rework and delay.
- Developer education: Real-time feedback helps developers learn secure coding practices.
Organizations with mature SAST programs report fewer security incidents, faster release cycles, and reduced security debt over time.
Building Developer Trust
Successful SAST implementation empowers developers rather than hindering them. Modern SAST tools integrate directly into development workflows, providing immediate feedback as code is written.
This shift-left approach transforms security from a bottleneck into a collaborative process. Developers gain confidence in their code’s security posture before submitting for review.
Vulnerability Identification: Common Security Issues Detected by SAST
Key Vulnerability Categories and Detection Capabilities
SAST tools excel at identifying a wide range of vulnerabilities, including:
- Injection flaws: SQL injection, XSS, command injection
- Authentication issues: Weak password handling, session management flaws
- Access control weaknesses: Insufficient authorization checks
- Cryptographic failures: Weak algorithms, improper implementation
- Security misconfigurations: Default settings, unnecessary features
These vulnerabilities align with industry standards like the OWASP Top 10 and CWE/SANS Top 25.
Language-Specific Vulnerabilities
Different programming languages have unique security challenges. SAST tools with language-specific analysis capabilities can detect:
- C/C++: Buffer overflows, memory leaks, use-after-free errors
- Java/C#: Deserialization issues, LDAP injection, XML external entities
- JavaScript/TypeScript: Prototype pollution, DOM-based XSS, unsafe eval usage
- Python: Path traversal, pickle deserialization, template injection
Comprehensive SAST solutions understand these language-specific nuances to provide accurate, relevant results.
SAST vs. Other Security Testing Methodologies: A Comparative Analysis
Comprehensive Security Testing Approaches and Their Relationships
SAST is just one component of a comprehensive application security testing strategy:
- SAST: Analyzes source code without execution
- DAST: Tests running applications from the outside
- IAST: Monitors application behavior during runtime
- SCA: Identifies vulnerabilities in third-party components
Each approach has distinct strengths and limitations. SAST excels at early detection and comprehensive code coverage, while other methods provide runtime validation or third-party component analysis.
Complementary Approaches
The most effective security programs combine multiple testing methodologies:
- SAST identifies issues early in development
- DAST validates security in running applications
- IAST provides detailed runtime vulnerability information
- SCA addresses supply chain security concerns
Together, these approaches provide defense in depth throughout the software development lifecycle.
SAST Implementation Best Practices: Integration Points and Success Factors
Strategic SDLC Integration Points for Maximum Effectiveness
Integrating SAST at the right points in your development process is crucial:
- IDE integration: Catch issues as developers write code
- Pre-commit hooks: Prevent vulnerable code from entering version control
- CI/CD pipeline: Verify security before deployment
- Scheduled scans: Maintain security oversight of the entire codebase
Early integration catches issues when they’re easiest and cheapest to fix.
Overcoming Adoption Hurdles
Given the many benefits SAST provides during the development process, there are also a few challenges that are easily overcome through basic configuration and implementation procedures. These include:
- False positives: Configure tools properly and tune rules
- Performance concerns: Implement incremental scanning for large codebases
- Developer resistance: Focus on education and demonstrate value
- Legacy code: Prioritize high-risk areas and establish baselines
Successful implementation requires both technical configuration and organizational change management.
Advanced SAST Capabilities: Whole-Program Analysis and Comprehensive Scanning
Benefits of Deep Analysis vs. Traditional Scanning Approaches
Basic SAST tools analyze code files in isolation, missing complex vulnerabilities that span multiple components. Deep SAST takes a different approach:
- Whole-program analysis: Examines interactions between components
- Cross-module visibility: Tracks data flow across application boundaries
- Context-aware scanning: Understands the purpose and behavior of code
- Semantic understanding: Recognizes vulnerable patterns beyond syntax
This comprehensive approach finds vulnerabilities that simpler tools miss entirely.
Multi-Language Support Matters
Modern applications rarely use a single programming language. Deep SAST solutions must analyze interactions between:
- Frontend and backend components
- Legacy and modern codebases
- Compiled and interpreted languages
- Custom code and third-party libraries
Comprehensive language support ensures no vulnerable code flies under the radar.
SAST Solution Selection Criteria: Essential Features and Capabilities
Key Evaluation Factors for Effective SAST Tools
When evaluating SAST tools, consider these essential capabilities:
- Remediation guidance: Help for developers fixing issues
- Analysis depth: Whole-program vs. file-by-file scanning
- Language coverage: Support for your technology stack
- Integration options: Compatibility with your development tools
- Accuracy: False positive and false negative rates
- Scalability: Performance with large codebases
- Reporting: Clarity and actionability of results
The right tool balances comprehensive security coverage with developer usability.
Integration Is Key
Look for SAST solutions that integrate seamlessly with your existing development environment:
- IDE plugins: Immediate feedback during coding
- CI/CD tools: Automated scanning in build pipelines
- Issue trackers: Streamlined remediation workflows
- Collaboration platforms: Shared visibility for teams
Strong integrations reduce friction and promote developer adoption.
CodeSonar: Advanced SAST Solution for Complex Development Environments
Superior Vulnerability Detection Through Comprehensive Analysis
CodeSonar delivers deep SAST capabilities that identify vulnerabilities other tools miss:
- Whole-program analysis: Finds issues that cross component boundaries
- Advanced code understanding: Recognizes complex vulnerability patterns
- Context-aware scanning: Minimizes false positives while maximizing detection
- Unique inspection reporting: Helps developers understand and prioritize issues
These capabilities enable security teams to find and fix critical vulnerabilities before they reach production.
Multi-Language Mastery
CodeSonar includes comprehensive support for modern development stacks:
- C/C++: Deep analysis of memory management and pointer issues
- Java/C#/Kotlin: Detection of framework-specific vulnerabilities
- Python/Go/Rust: Coverage for both compiled and interpreted languages
- JavaScript/TypeScript: Frontend security analysis
This broad language support ensures consistent security across your entire application portfolio.
DevSecOps at Speed and Scale
CodeSonar was built for modern development environments:
- Support for 100+ compilers and compiler versions
- Numerous integrations with popular development tools and IDEs
- OASIS SARIF support for seamless information exchange
- Scalable analysis for large, complex codebases
These capabilities make CodeSonar an ideal foundation for DevSecOps transformation, helping teams release solutions faster and with fewer defects.
Standards Compliance Made Simple
CodeSonar supports all major coding standards and is pre-qualified for:
- IEC 61508: Functional safety for electrical/electronic/programmable systems
- ISO 26262: Automotive functional safety
- EN 50128: Railway applications
- DO-178C/DO-330: Avionics systems
The tool also supports MISRA, AUTOSAR, JSF++, CWE, and CERT coding standards, making compliance verification straightforward and comprehensive.
Getting Started with SAST: Implementation Strategy and Roadmap
Organizational Assessment and Requirements Analysis
Begin your SAST implementation by evaluating:
- Your technology stack and programming languages
- Development workflow and integration points
- Compliance and regulatory requirements
- Team size and security expertise
These factors will guide your tool selection and implementation approach.
Building Your Implementation Roadmap
Successful SAST adoption follows a clear progression:
- Pilot phase: Start with a small, critical project
- Tool configuration: Tune for your codebase and risk profile
- Developer training: Ensure teams understand findings and remediation
- Pipeline integration: Automate scanning in your CI/CD workflow
- Metrics establishment: Measure security improvements over time
This phased approach builds confidence and demonstrates value throughout the implementation process.
Maximizing Your Investment
To get the most from your SAST program:
- Focus initial remediation on critical vulnerabilities
- Integrate security education into developer onboarding
- Establish clear SLAs for vulnerability remediation
- Regularly review and update scanning rules
- Track and celebrate security improvements
These practices transform SAST from a security tool into a competitive advantage.
Ready to Explore CodeSonar?
Experience the difference deep SAST can make in your application security program. CodeSonar delivers comprehensive vulnerability detection, developer-friendly workflows, and the insights you need to secure your applications effectively.
- Download our Data Sheet to learn more about CodeSonar’s capabilities
- Request a Trial to see CodeSonar in action with your own code
- Contact our security experts to discuss your specific requirements
Take the next step in your application security journey with CodeSonar, the SAST solution that finds vulnerabilities others miss.
download pdf