Executive Summary: The Critical Need for Advanced Embedded Code Analysis
Bottom Line: With the embedded software market growing at 9.5% annually through 2030, the stakes for quality assurance have never been higher. This rapid expansion, fueled by connected devices and IoT solutions, means embedded systems are deployed in increasingly critical applications where software failures can have catastrophic consequences, making adherence to quality standards like MISRA C not just best practice, but business-critical.
The quality and security of embedded applications are the gold standard for excellence in software development. This is because embedded applications perform functions that are essential to safety-critical activities, countless times per day. Unlike enterprise software failures that result in downtime or data loss, embedded system vulnerabilities can cause catastrophic physical harm, regulatory penalties, and brand destruction.
The convergence of several factors is creating an urgent need for advanced embedded code analysis. The growing size of code bases means additional complexity for developers to deal with, and complexity, in turn, translates to a higher incidence of defects. Simultaneously, the rapid trend toward networking in embedded systems has created larger attack surfaces for malicious hackers to exploit.
The regulatory landscape is intensifying. The movement toward formal product development standards, such as MISRA, DO-178B/C, or ISO 26262, continues to grow worldwide. MISRA C influences standards across many industries where critical software is built. MISRA C guidelines are either directly cited by or commonly practiced in projects following AUTOSAR, IEC 62304, IEC 61508, ISO 26262, and DO-178C processes.
The solution requires a fundamental shift in approach. Traditional static analysis tools designed for enterprise web applications are insufficient for embedded environments. Development leaders need solutions that provide whole-program, path-sensitive analysis capable of detecting complex defects across module boundaries, handling legacy binary code, and ensuring compliance with evolving safety standards like MISRA C:2025.
This white paper outlines six critical best practices that successful embedded development teams implement to achieve both rapid development cycles and uncompromising safety standards.
The Embedded Software Challenge Landscape: Why Traditional Analysis Falls Short
Safety-Critical vs. Enterprise Software: The Stakes
The fundamental difference between embedded and enterprise software lies not just in their deployment environments, but in their failure consequences. While the demands to build a reliable trading platform, enterprise HR application, or CRM system are high, the pressure to build a reliable pacemaker, automotive automatic braking system, or nuclear control system is extraordinary.
Therefore, on rare occasions when these systems do fail, the repercussions are significant and often damaging. A buffer overflow in a web application might enable data theft; the same vulnerability in an automotive braking system could cause fatal accidents. This reality demands analysis approaches that prioritize safety and security over speed of implementation.
The 30% Annual Growth Challenge
Development teams face an unprecedented scaling challenge. Embedded development teams use a mix of waterfall and agile methodologies. Whichever coding philosophy a team believes in, every developer today is facing increased demand for faster cycles to add new features, respond to customer feedback, and fix known bugs.
This growth isn’t just about lines of code—it’s about interaction complexity. Modern embedded systems integrate multiple processors, real-time operating systems, network stacks, and third-party components. Each integration point creates potential failure modes that traditional syntactic analysis tools cannot detect.
Legacy Code Integration Complexities
Unlike greenfield enterprise applications, embedded systems often must integrate decades-old legacy code. Embedded systems come with legacy codebases that were written before modern security practices existed. These systems may lack source code documentation, use deprecated language features, or integrate binary-only third-party components.
Foundation Best Practice: Establish Comprehensive Coding Standards
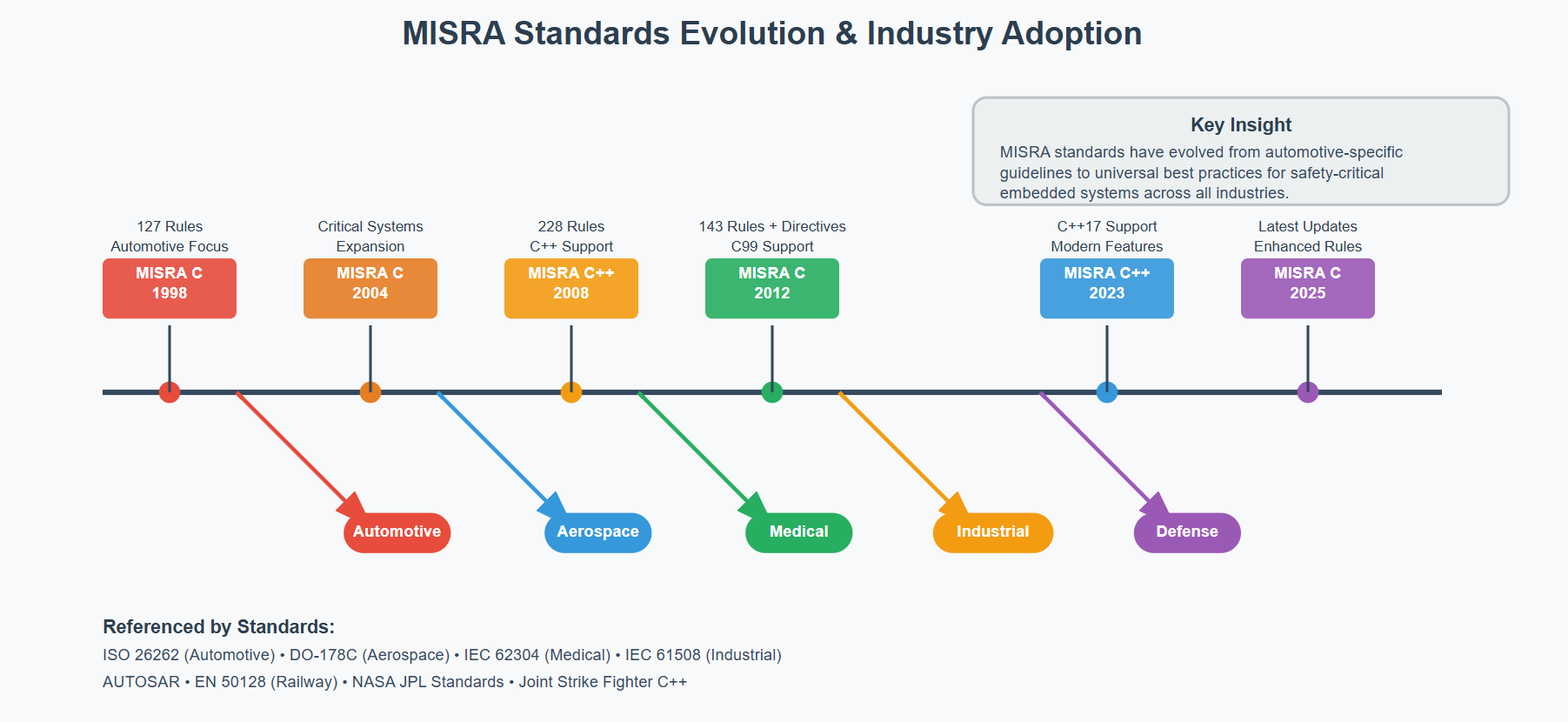
Understanding the MISRA Evolution
The bedrock of embedded security starts with coding standards. The MISRA Working Group developed the MISRA C guidelines to establish best practices in coding, tools, and development processes to ensure the reliability, safety, and security of embedded software in critical systems.
MISRA has evolved significantly from its automotive origins. Although originally specifically targeted at the automotive industry, MISRA C has evolved as a widely accepted model for best practices by leading developers in sectors including automotive, aerospace, telecom, medical devices, defense, railway, and others.
The latest iteration brings critical updates. CodeSonar 9.1 delivers an improved user experience for analyzing Android, new Kotlin checkers, and increased standards coverage, including the new MISRA-C 2025 guidelines. The newly released MISRA C:2025 rule set is by no means as big – more of a tweaking of the MISRA C:2023 rules – but it does have a few changes which are worth exploring.
Multi-Standard Compliance Strategy
Modern embedded systems require multi-layered compliance approaches. MISRA C guidelines are either directly cited by or commonly practiced in projects following AUTOSAR, IEC 62304, IEC 61508, ISO 26262, and DO-178C processes. Industry-specific standards like the Joint Strike Fighter C++ Coding Standard and the NASA Jet Propulsion Library C Coding Standard have incorporated MISRA principles into their own frameworks, demonstrating the widespread influence of MISRA’s safety-focused approach across different programming languages and domains.
In addition to improving the security and safety of embedded systems, compliance with MISRA C has legal and financial benefits. Development leaders must understand that MISRA C is not a coding style guide but rather a set of rules and directives to minimize or eliminate coding practices known to be hazardous. The standards address fundamental C language limitations where the implementation and behavior of some features are not specified to give compilers, operating systems, and developers flexibility in their use.
Setting Realistic Baselines for Legacy Code
The most effective teams don’t attempt perfect compliance immediately. By setting baselines, you can focus on making sure your new code is compliant. This approach acknowledges the reality that you could have hundreds or even thousands of violations in your code.
Smart teams implement a risk-based prioritization strategy. You need to know the MISRA coding rules pertinent to which version of C or C++ you’re using and prioritize violations based on risk.
Best Practice: Implement Deep Static Analysis
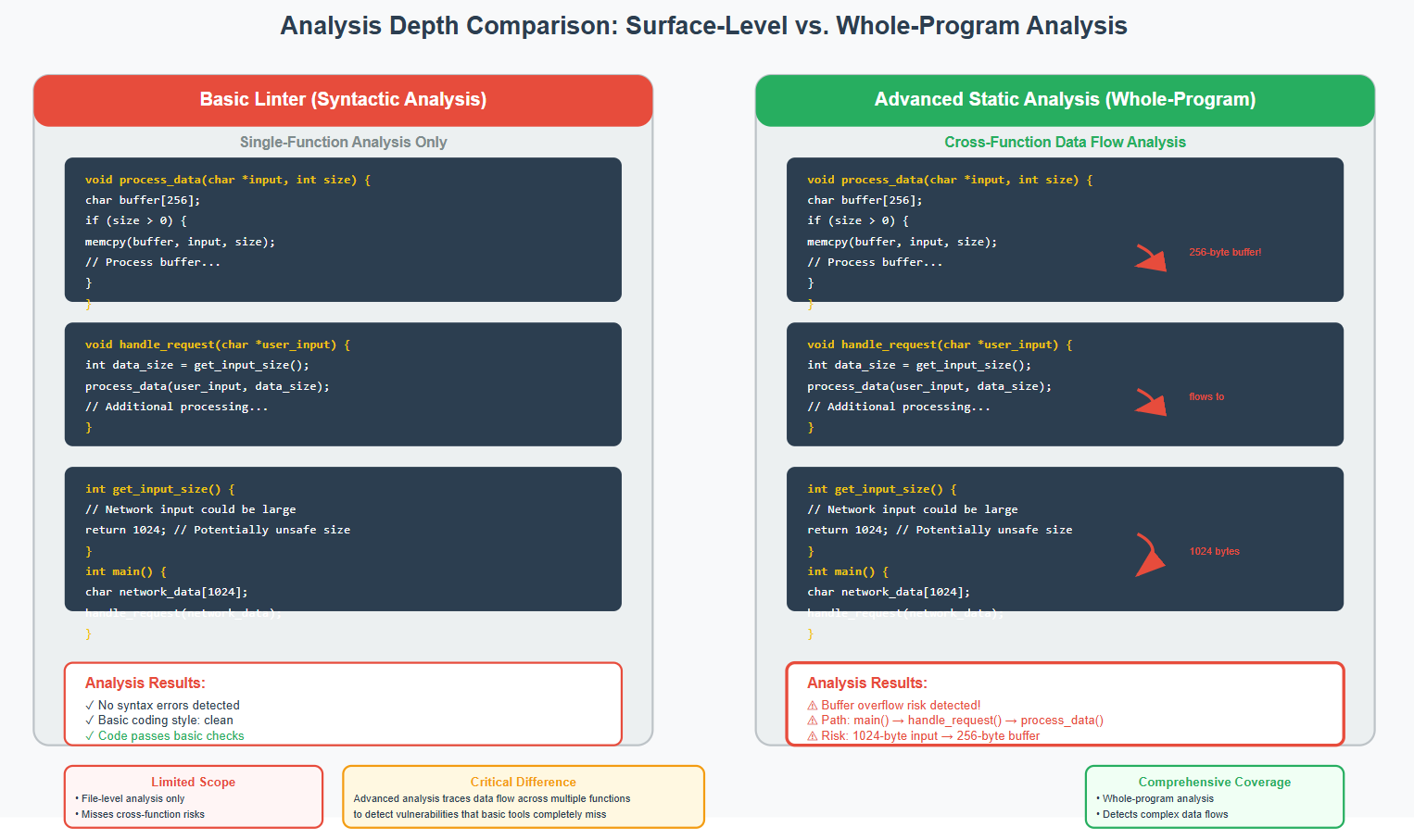
Path-Sensitive vs. Syntactic Analysis
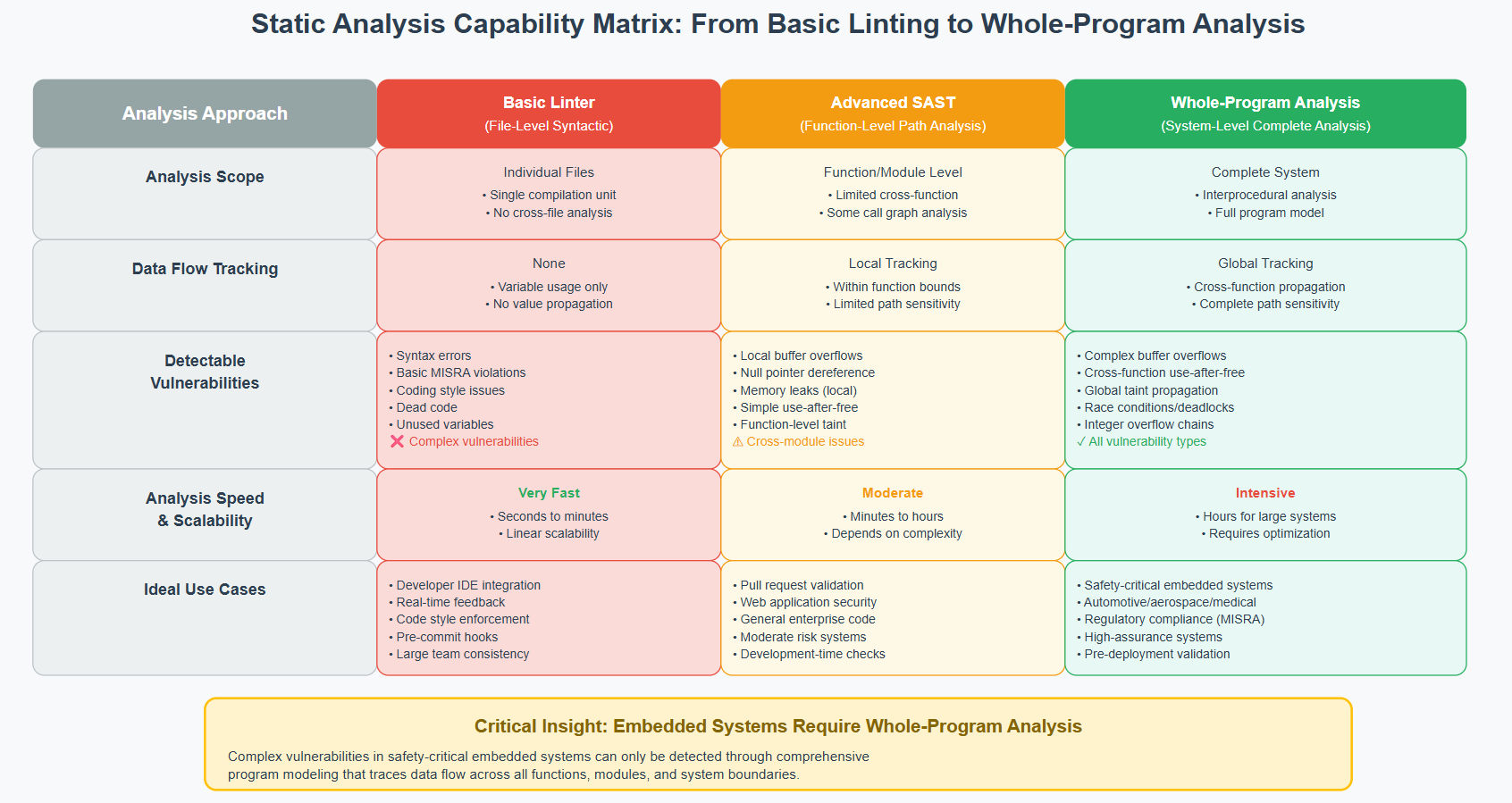
The difference between effective and ineffective static analysis lies in analytical depth. Most traditional tools perform shallow syntactic checks—essentially advanced linters that identify obvious rule violations. However, embedded systems require whole-program, path-sensitive analysis that can trace data flow across multiple functions and modules.
Some C compilers can identify risky coding implementations, but they are by no means as comprehensive or effective as automated tools that can identify issues earlier in the lifecycle. Advanced static analysis tools build abstract representations of entire programs, enabling them to detect complex issues like buffer overflows that occur through intricate interaction patterns.
Consider this critical distinction: Organizations in these industries must be equipped to identify not only the violations of superficial syntactic rules but also serious bugs arising from undefined behavior, for example, as proscribed by the MISRA C:2012 standard.
Undefined Behavior Detection
The C language’s flexibility creates numerous opportunities for undefined behavior. One common source of such problems involves type mismatches and inconsistent data handling, where variables of different types interact in ways the C standard doesn’t fully specify. Such type inconsistencies are prohibited by the standard because they can cause silent truncations and overflows that can lead to unexpected behavior.
These unspecified features can lead to behaviors at runtime that are: Undefined – the C standard contains no requirement for how the feature must behave. Unspecified – the C standard allows for two or more behaviors for a feature with no specification as to which one shall be used.
Advanced static analysis tools must detect these subtle issues that only manifest under specific runtime conditions. While some of these occurrences can be enumerated through testing, only the most advanced static-analysis tools are capable of finding the more subtle occurrences.
Best Practice: Integrate Security-First Development
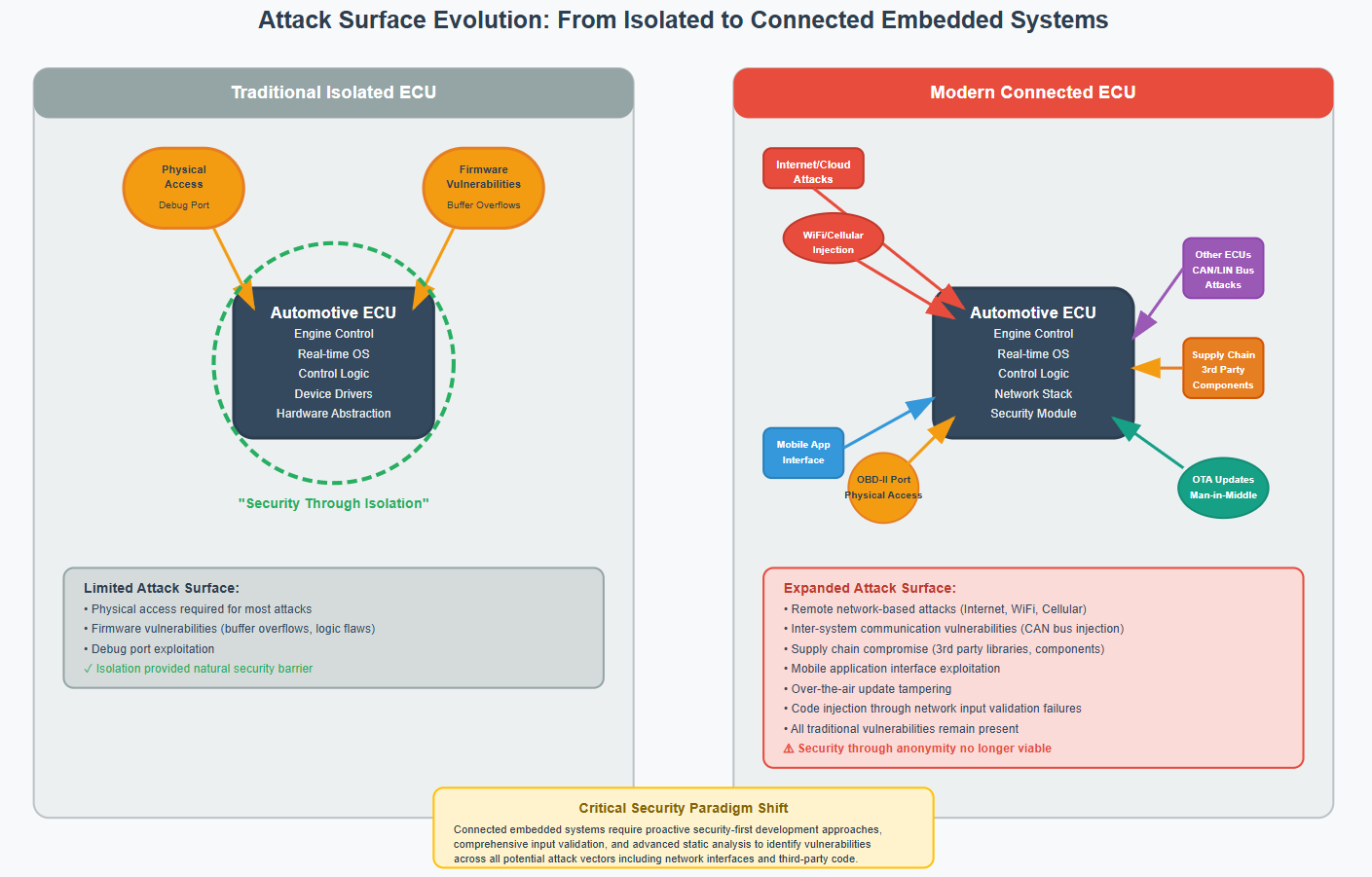
Taint Analysis for IoT-Connected Systems
The security landscape for embedded systems has fundamentally changed. The rapid trend toward networking in embedded systems has created larger attack surfaces for malicious hackers to exploit. Development teams can no longer rely on the “security through obscurity” that characterized isolated embedded systems.
Code-injection attacks succeed when a malicious attacker feeds specially-crafted input data over an input channel to a program that fails to check that the data is well-formed and within reasonable bounds, and then passes it through to a sensitive part of the program.
Modern embedded security requires treating all external input as potentially malicious. Programmers can defend against these vulnerabilities by treating input data as potentially hazardous (tainted) and validating it before the application is allowed to act on it.
Code Injection Prevention Strategies
Input validation in embedded systems presents unique challenges compared to web applications. Resource constraints limit the sophistication of validation routines, while real-time requirements demand that security checks execute within strict timing bounds.
Effective teams implement defense-in-depth strategies that combine compile-time analysis with runtime protection mechanisms. This includes bounds checking, input sanitization, and privilege separation where system architecture permits.
Supply Chain Security for Embedded Components
Third-party component security has become a critical concern. Modern embedded systems integrate components from multiple vendors, creating potential supply chain vulnerabilities. Teams must implement analysis strategies that can assess the security posture of both open-source and commercial components.
This requires both static analysis of available source code and binary analysis of compiled components to identify potential backdoors, vulnerable functions, or poor coding practices that could compromise system security.
Best Practice: Automate Continuous Compliance
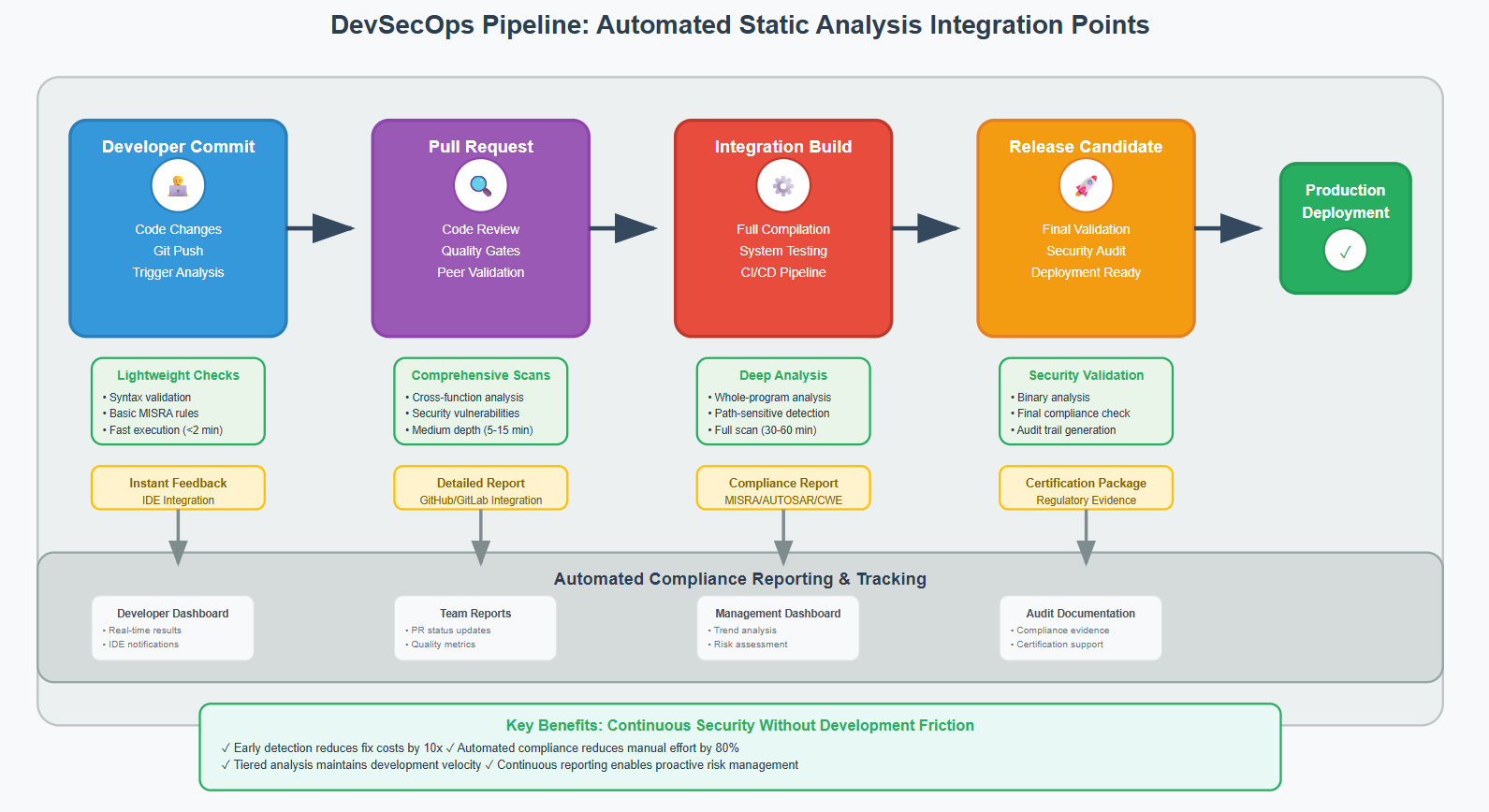
CI/CD Integration Without Slowing Development
The challenge: maintaining rigorous analysis without breaking development velocity. Every developer today is facing increased demand for faster cycles to add new features, respond to customer feedback, and fix known bugs. Traditional approaches that require lengthy manual security reviews conflict with modern development expectations.
Successful teams implement tiered analysis strategies: lightweight checks for every commit, comprehensive analysis for integration builds, and deep security reviews for release candidates. This approach catches obvious issues early while reserving expensive deep analysis for critical checkpoints.
The key insight: Continuously inspecting your code for violations is the best way to improve quality. Automated systems can perform this inspection without human intervention, enabling teams to maintain both speed and quality.
Automated Compliance Reporting
Regulatory compliance requires auditable evidence trails. Regulatory agencies may require adherence to these standards, but even if not, they are widely recognized as best practices. Manual compliance reporting is time-intensive and error-prone.
Advanced teams implement automated reporting systems that generate compliance evidence as part of the build process. These systems track rule violations, document deviation approvals, and maintain historical compliance trends—all critical for regulatory audits.
Risk-Based Violation Prioritization
Not all violations carry equal risk. You could have hundreds or even thousands of violations in your code, making manual triage impossible at scale. Effective prioritization systems consider multiple factors: severity of the potential defect, likelihood of exploitation, system criticality, and remediation complexity.
Smart teams focus first on violations that could cause safety issues, then security vulnerabilities, followed by quality and maintainability concerns. This approach ensures that limited development resources address the most critical risks first.
Best Practice: Tool Selection and Team Enablement
Whole-Program Analysis Capabilities
Tool selection fundamentally determines analysis effectiveness. Choosing the right static code analyzer makes everything else easy. However, many organizations focus on feature checklists rather than analytical depth.
The critical capability difference lies in whole-program analysis. Basic tools analyze individual files or functions in isolation. Advanced tools build comprehensive program models that enable cross-module defect detection. This capability is essential for embedded systems where critical functionality often spans multiple compilation units.
Teams should evaluate tools based on their ability to detect interprocedural defects: buffer overflows that occur through complex calling sequences, use-after-free bugs that span multiple functions, and concurrency issues in multi-threaded embedded systems.
Multi-Language Support
Modern embedded systems are inherently polyglot. While C and C++ remain dominant for real-time control code, systems increasingly integrate Python scripts, Java applications, and JavaScript interfaces. Many MISRA C rules can be characterized as guidelines because under certain condition software engineers may deviate from rules and still be considered compliant with the standard.
Comprehensive language support enables unified analysis workflows. Teams benefit from tools that can analyze multiple programming languages within a single platform, providing consistent vulnerability detection and compliance reporting across the entire system stack.
Team Training and Adoption Strategies
Technology adoption succeeds or fails based on team acceptance. The MISRA standard also stresses competency, expertise, and training of staff as key factors for evaluating product readiness. This includes recognizing the risks of violations, and properly configuring and using development tools and static analysis.
Successful deployments focus on developer workflow integration rather than standalone security reviews. Teams that integrate analysis results directly into IDEs, code review processes, and issue tracking systems see higher adoption rates and faster issue resolution.
The training challenge is significant. Developers must understand not just how to use analysis tools, but how to interpret results, prioritize findings, and make appropriate risk-based decisions about violations and deviations.
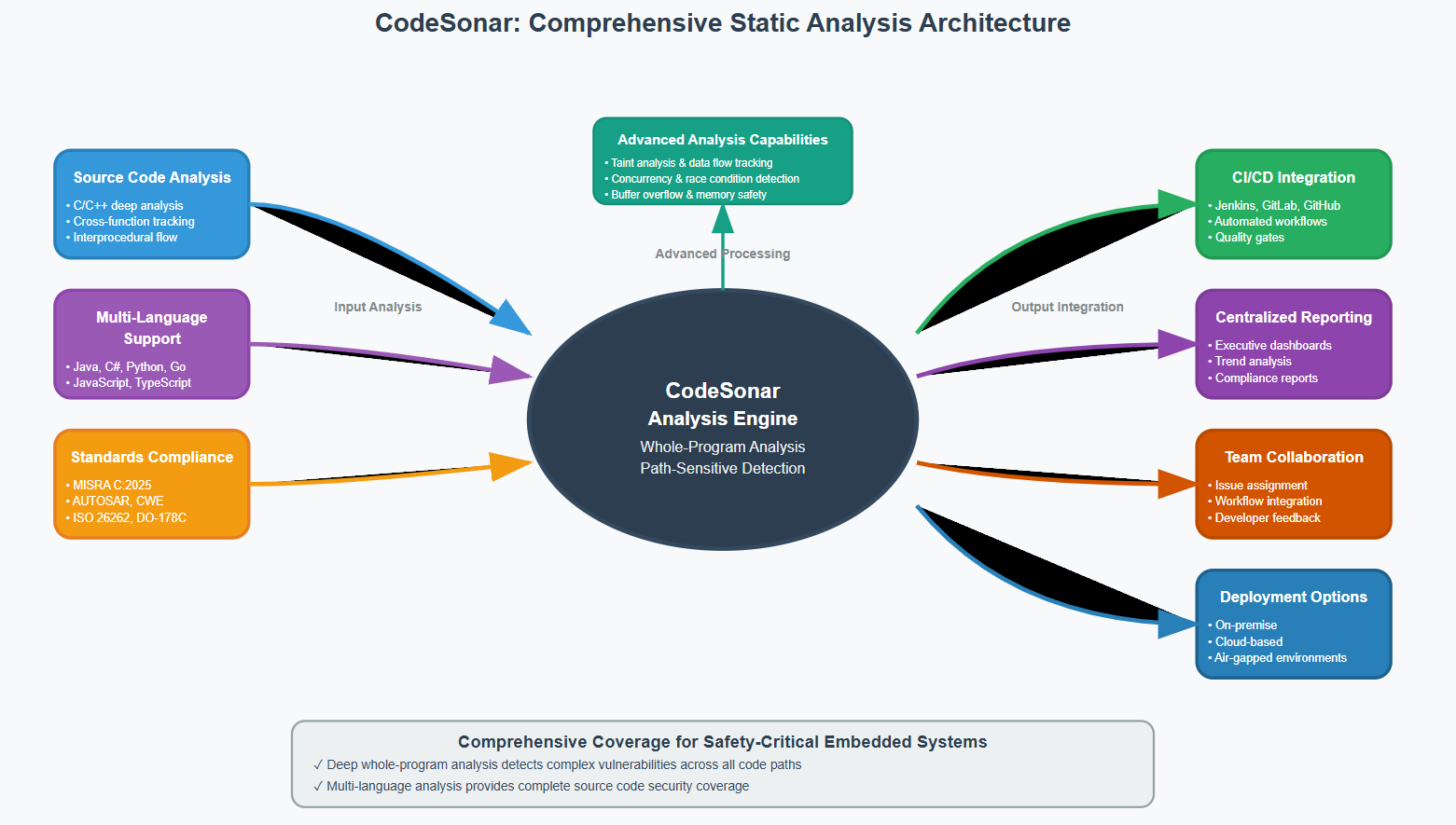
CodeSonar 9.1: Implementing Best Practices at Scale
Deep, Whole-Program Analysis for Modern Embedded Development
CodeSonar distinguishes itself by providing deep, whole-program, path-sensitive analysis with exceptional support for safety-critical embedded environments. Unlike tools focused primarily on web security or lightweight syntactic checking, CodeSonar builds highly accurate abstract representations of complete applications to examine all execution paths and identify complex defects.
The analytical depth advantage is significant. CodeSonar’s advanced analysis engine handles the largest codebases while helping developers pinpoint defects with greater precision. This includes detection of buffer overflows, use-after-free vulnerabilities, concurrency issues, and undefined behavior that can only be identified through comprehensive program modeling.
MISRA C:2025 and Multi-Standard Coverage
CodeSonar 9.1 delivers comprehensive coverage of evolving safety standards. Coverage of MISRA-C 2025. Improved Android analysis without downloading extra scripts. Increased AUTOSAR 14 and MISRA-C++ 2023 coverage. More Kotlin checkers. Support for .NET 9.
The platform provides built-in compliance reporting for critical standards including MISRA, OWASP, CWE, and industry-specific requirements. Category and taxonomy reports, such as MISRA or AUTOSAR reports, now include a summary section with alerts, summary, and category information.
Functional safety certification provides additional assurance. CodeSonar is pre-qualified for the highest levels of safety for IEC 61508, ISO 26262, and CENELEC EN 50128 standards, with artifacts available for DO-178C/DO-330 qualification.
Enhanced Android and Multi-Language Analysis
Modern embedded systems require multi-language support. CodeSonar 9.1 expands capabilities across C/C++, Java, C#, Kotlin, Python, Go, Rust, JavaScript, and TypeScript. Improved support for analyzing new C and C++ 26 language features. Added support for clang 19 and 20.
The enhanced Android analysis capabilities address the growing complexity of embedded systems that integrate Android-based interfaces with real-time control systems, eliminating the need for additional scripting while providing comprehensive security coverage.
Enterprise Integration and Scalability
CodeSonar integrates seamlessly with modern DevSecOps environments. The platform works in air-gapped, on-premise, distributed, and cloud-based CI/CD environments, supporting parallel and distributed build systems for maximum scalability. CodeSonar Docker images and helm charts are available from a secure container registry.
The platform’s comprehensive reporting and visualization capabilities help development teams understand complex defect paths, assess risk severity, and maintain compliance evidence for regulatory audits.
Learn More: Contact the CodeSonar team to discover how CodeSonar 9.1 can transform your embedded development security posture while maintaining development velocity.
Book a Demo