DevSecOps Methodology Demystified: Security From Day One
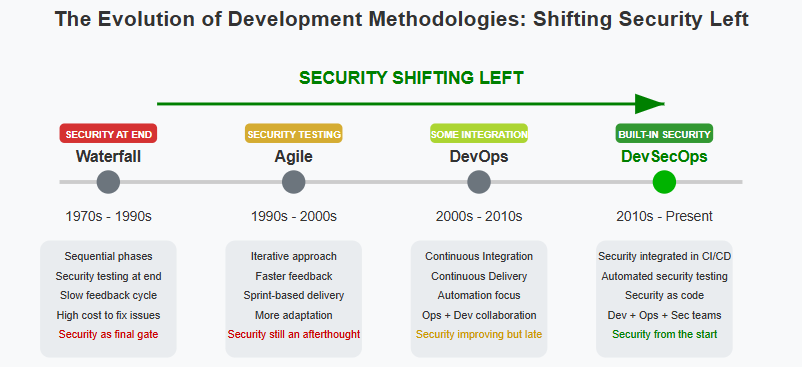
DevSecOps represents a transformative approach to software development that integrates security practices throughout the entire DevOps lifecycle. Rather than treating security as a final checkpoint, DevSecOps weaves protection measures directly into every stage of development.
This evolution from traditional DevOps emerged as organizations recognized that bolting security on at the end was both inefficient and risky. By incorporating security from the beginning, teams can identify vulnerabilities earlier when they’re less costly to fix.
At its core, DevSecOps embraces the “shift left” philosophy, moving security considerations earlier in the development timeline. This proactive stance transforms security from a bottleneck into a built-in feature of high-quality software.
Core Principles of DevSecOps
DevSecOps isn’t just a methodology, it’s a mindset shift. It values automation over manual security checks, favoring repeatable processes that can scale with development needs.
Collaboration sits at the heart of this approach, breaking down traditional silos between development, operations, and security teams. When these groups work together, security becomes everyone’s responsibility.
Continuous improvement drives DevSecOps forward, with each iteration enhancing both the product and its protective measures. This adaptive stance keeps security relevant in an ever-changing threat landscape.
The Business Case: Why DevSecOps Matters
Protecting Your Business and Customers
Implementing DevSecOps dramatically strengthens your security posture, helping you meet compliance requirements across various regulatory frameworks. This systematic approach creates auditable security processes that satisfy even the most stringent standards.
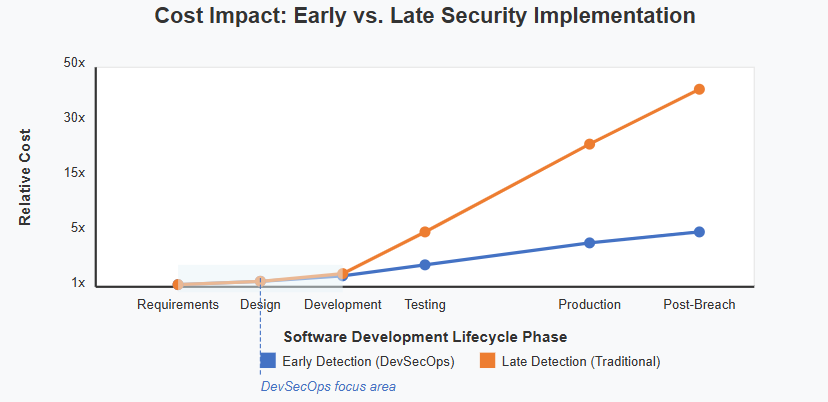
Early vulnerability detection translates directly to cost savings. Research shows fixing a security issue during development costs a fraction of remediation after deployment, as much as 30 times less expensive.
DevSecOps also accelerates time-to-market while maintaining robust security. By automating security checks, teams can deliver features faster without compromising protection.
Better Teams, Better Products
Cross-functional collaboration breaks down organizational barriers, creating a unified approach to product security. When developers understand security implications and security professionals appreciate development constraints, better solutions emerge.
This collaborative environment fosters shared ownership of security outcomes, leading to higher quality products and more secure code overall.
Cautionary Tales
Consider the 2017 Equifax breach that exposed 147 million Americans’ personal data. A timely security patch implementation, standard practice in DevSecOps, could have prevented this massive compromise.
Similarly, the SolarWinds supply chain attack demonstrated how security gaps in the development pipeline can have cascading effects across thousands of customers. DevSecOps practices like code signing and integrity verification help prevent such incidents.
Building Your DevSecOps Framework
Automation: The Foundation of Secure Development
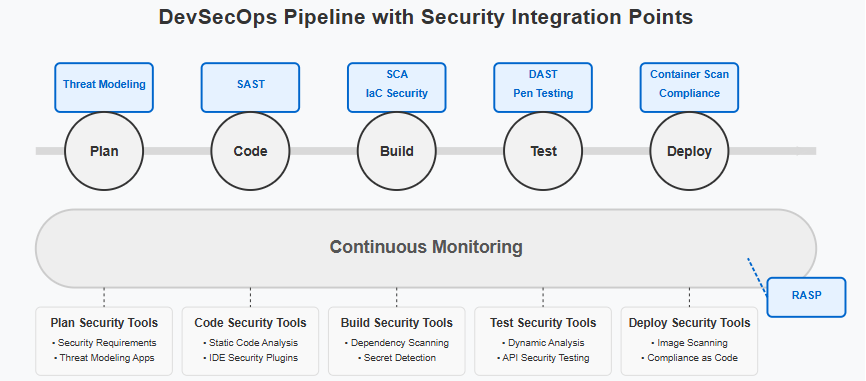
Security automation tools eliminate human error and ensure consistent protection across your codebase. From commit scanning to deployment verification, automated tools maintain security vigilance without slowing down development.
Continuous integration and continuous delivery pipelines become more robust with integrated security gates. These automated checkpoints verify that code meets security standards before advancing to the next stage.
Infrastructure as code security tools scan configuration files for misconfigurations before deployment, preventing common cloud vulnerabilities from reaching production.
Containers and Cloud: Securing Modern Infrastructure
Container security requires specialized approaches that address unique risks like base image vulnerabilities and runtime protection. Scanning tools integrated into your registry can prevent vulnerable containers from being deployed.
Cloud environments demand security controls specifically designed for dynamic, API-driven infrastructure. Cloud security posture management tools continuously monitor your environment for drift from secure configurations.
Comprehensive vulnerability management processes track issues from discovery through resolution, providing visibility into your security status across all environments.
The DevSecOps Journey: Implementation Roadmap
Starting Where You Are
Begin by thoroughly assessing your current development practices to identify security gaps. Document your existing workflows and note where security could be integrated without disrupting productivity.
Security culture-building is often the most challenging aspect of implementation. Start with small wins that demonstrate value to developers rather than imposing burdensome processes.
Tool selection should align with your technology stack and team capabilities. Prioritize tools that integrate seamlessly with existing workflows to minimize friction.
Building Security Fundamentals
Create clear security policies based on recognized standards like NIST or OWASP. These guardrails provide consistency while allowing teams to innovate within secure boundaries.
Developer security training should be practical and relevant to their daily work. Focus on secure coding patterns they can immediately apply rather than theoretical concepts.
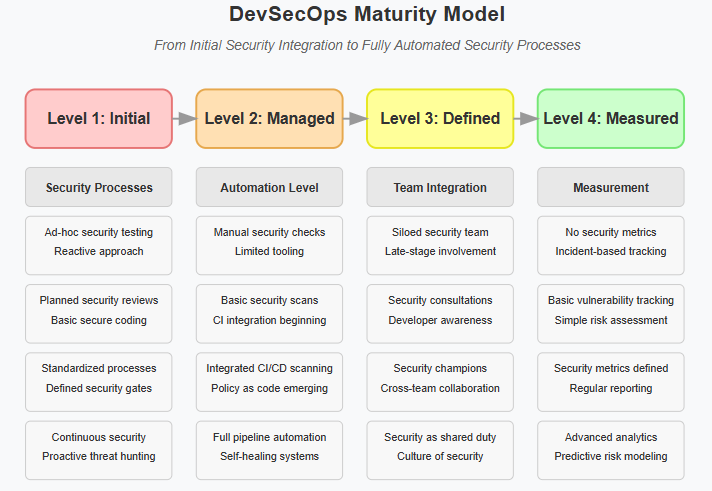
Establish concrete metrics to measure your DevSecOps progress, such as vulnerability remediation time, security test coverage, and deployment frequency.
Essential DevSecOps Toolkit
Code Analysis and Testing
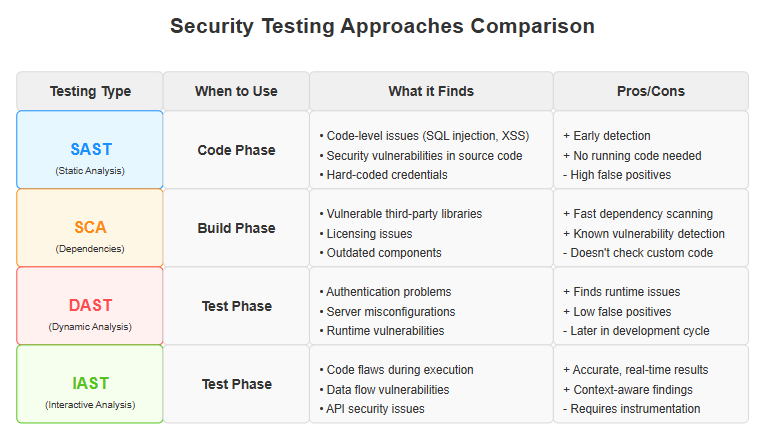
Static Application Security Testing (SAST) tools scan source code for security vulnerabilities without execution. These tools catch issues like injection flaws and insecure cryptography early in development.
Dynamic Application Security Testing (DAST) analyzes running applications by simulating attacks against exposed interfaces. This real-world testing finds vulnerabilities that might be missed in static analysis.
Interactive Application Security Testing combines both approaches, instrumenting applications to detect vulnerabilities during test execution for more accurate results.
Supply Chain and Infrastructure Security
Software Composition Analysis tools inventory and verify third-party components in your application. These scanners identify known vulnerabilities in dependencies before they affect your product.
Container scanning ensures that container images don’t include vulnerable components or misconfigured settings. Automated checks prevent insecure containers from reaching production.
Secret management solutions protect sensitive credentials throughout the development process. Centralized secret stores prevent hardcoded credentials and accidental exposure of sensitive information.
DevSecOps Best Practices: Excellence in Implementation
Proactive Security Measures
Automated security testing should occur at multiple points in your pipeline, creating defense in depth. Each stage provides different security perspectives, from code analysis to runtime protection.
Threat modeling during planning helps teams anticipate potential attacks before writing code. This proactive exercise identifies security requirements early when they’re easier to address.
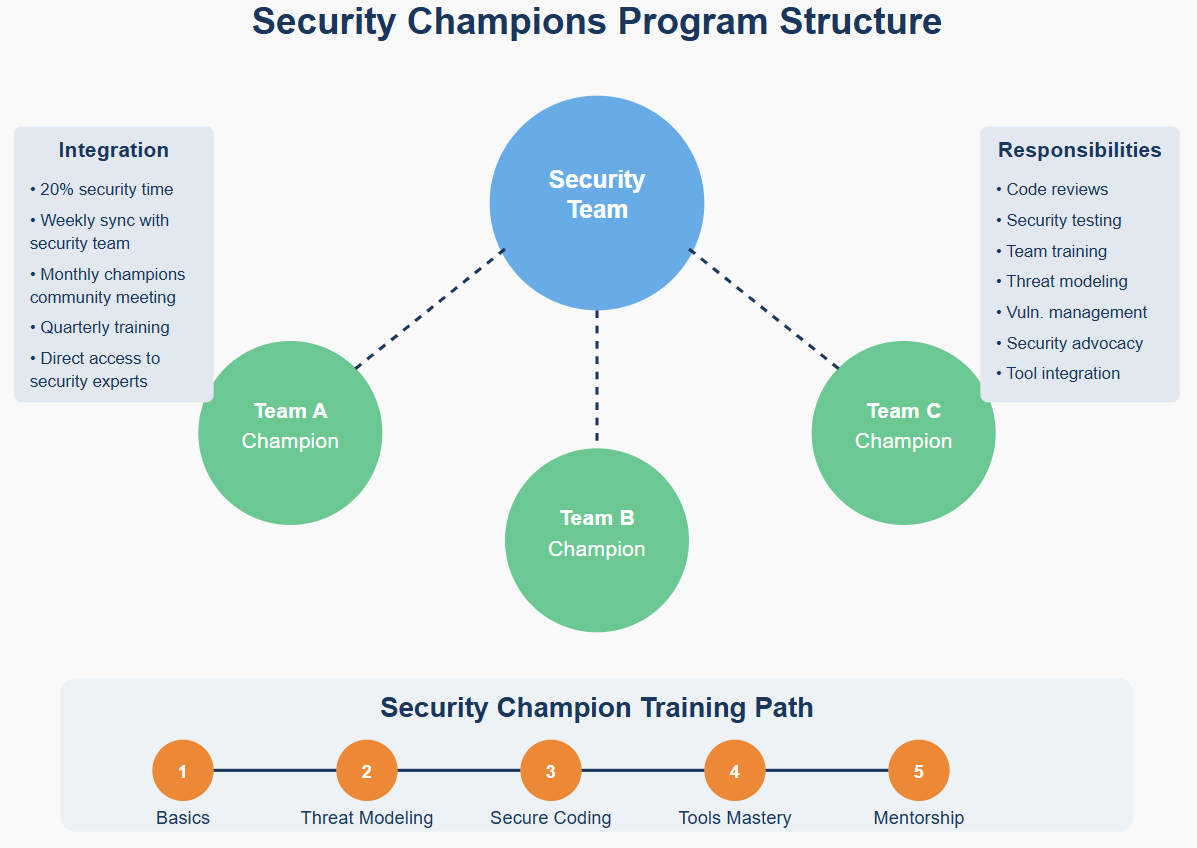
Security champions embedded within development teams serve as bridges between security and development. These advocates bring security expertise directly into daily development discussions.
Continuous Security Improvement
Regular security training keeps your team updated on emerging threats and protection techniques. Rotate topics regularly to maintain engagement and address evolving risks.
Post-deployment monitoring extends security beyond delivery, watching for unusual behavior that might indicate compromise. Robust logging and alerting help teams respond quickly to potential incidents.
\Feedback loops ensure lessons from security incidents improve future development. Blameless post-mortems help teams learn without creating a culture of fear around security issues.
Navigating Common DevSecOps Challenges
Cultural and Process Hurdles
Resistance from development teams often stems from concerns about productivity impacts. Address this by demonstrating how security automation actually reduces rework and improves code quality.
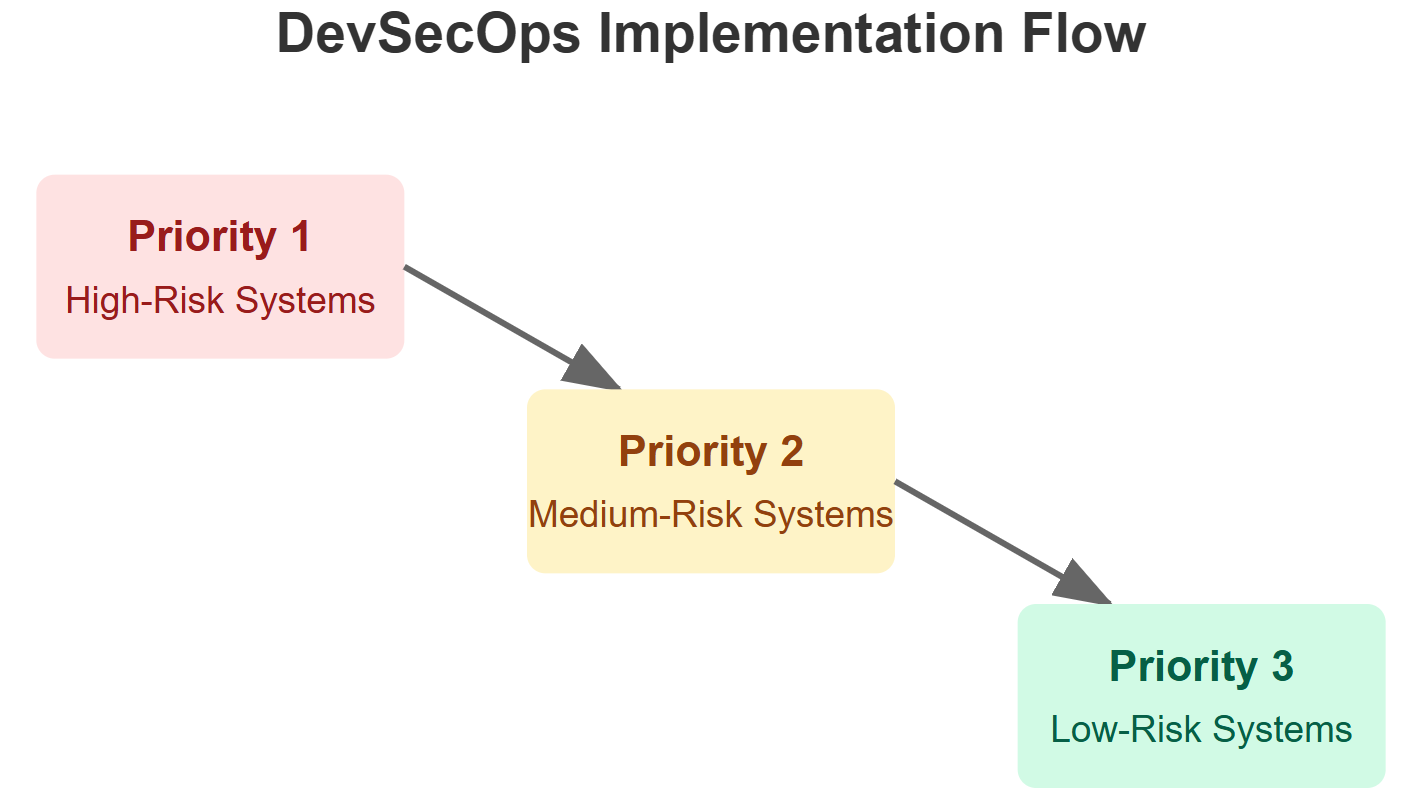
Balancing security with development velocity requires thoughtful integration. Focus on high-risk areas first and gradually expand coverage as teams adapt to security processes.
Tool sprawl creates confusion and technical debt. Aim for a consolidated toolchain with strong integration between components rather than point solutions for every security concern.
Technical Implementation Challenges
Security expertise gaps can slow adoption. Consider security-as-a-service options or specialized training to bridge knowledge deficits while building internal capabilities.
Legacy systems present unique security challenges that require custom approaches. Implement compensating controls while gradually moving toward more secure architectures.
Regulatory compliance across multiple jurisdictions demands a systematic approach. Map security controls to various requirements to identify overlaps and simplify compliance efforts.
DevSecOps Across Industries: Tailored Approaches
Industry-Specific Security Considerations
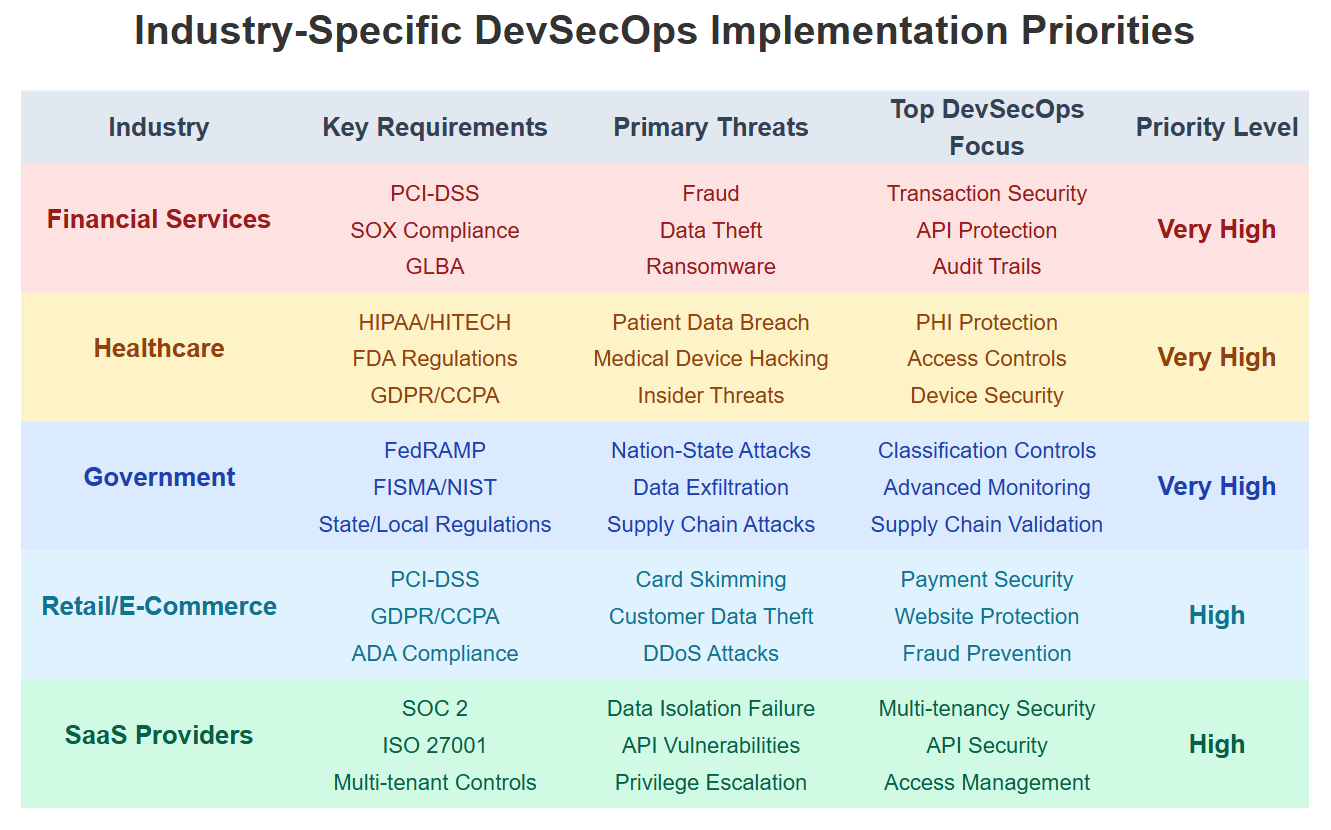
Financial services face strict regulations and constant attack attempts. Their DevSecOps implementations typically emphasize fraud prevention, data protection, and regulatory compliance.
Healthcare organizations must balance security with accessibility in life-critical systems. HIPAA compliance requirements shape their approach to patient data protection.
Government and public sector applications face sophisticated nation-state threats. Their DevSecOps practices incorporate stricter access controls and comprehensive audit capabilities.
Retail and e-commerce companies prioritize customer experience alongside security. Their approaches focus on protecting payment systems while maintaining performance.
SaaS providers build multi-tenant environments that require strong isolation between customers. Their DevSecOps practices emphasize infrastructure security and access management.
The Future of Secure Development
Emerging Security Paradigms
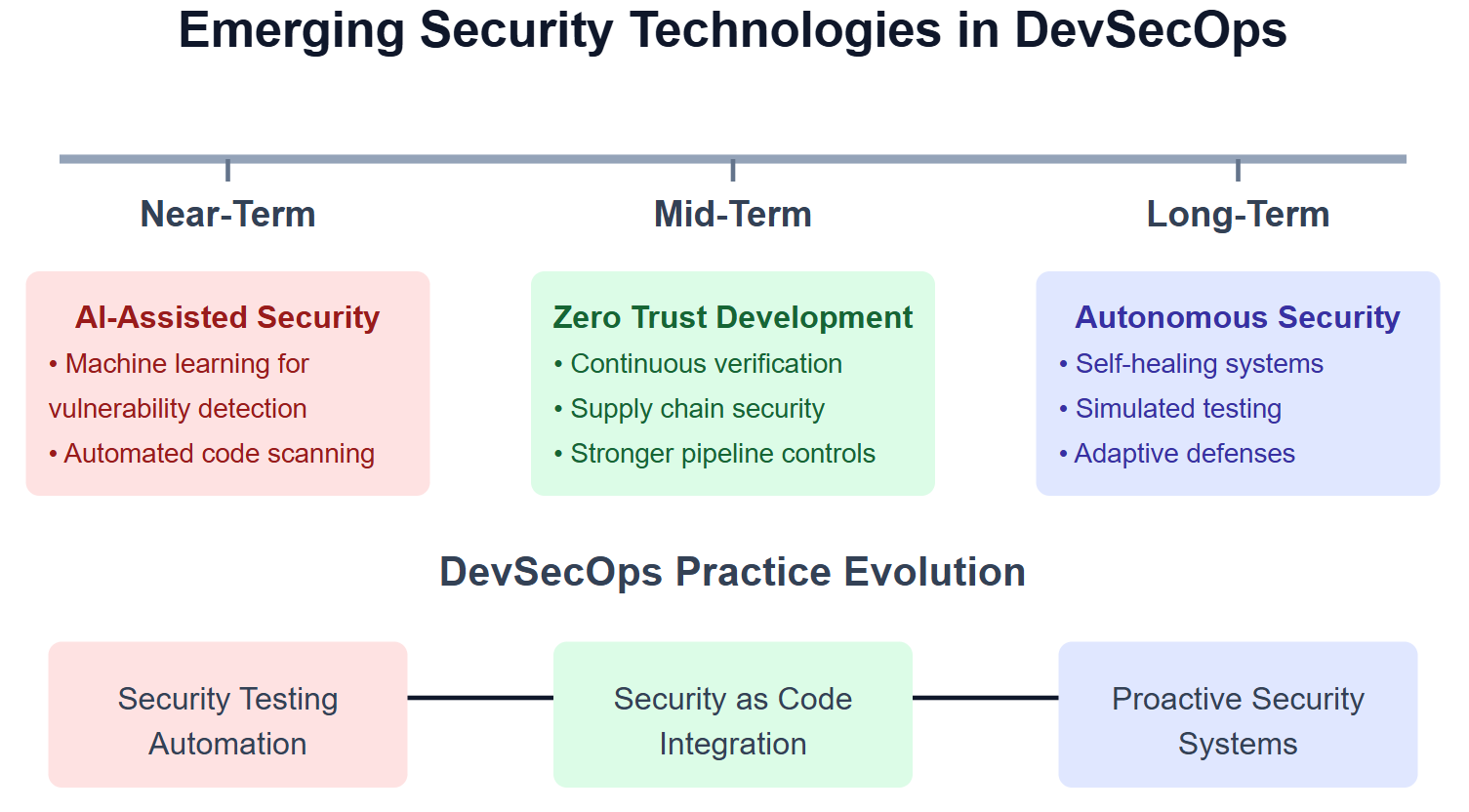
AI and machine learning are revolutionizing security through predictive vulnerability detection. These technologies identify potential weaknesses based on code patterns before exploits emerge.
Zero trust architecture principles are being woven into DevSecOps practices, requiring continuous verification of every system component. This approach limits lateral movement in case of compromise.
The industry is gradually shifting from discrete “DevSecOps” towards universally integrated security. As practices mature, security will become an inseparable aspect of software development.
Adapting to Tomorrow’s Threats
The evolving threat landscape demands continuous adaptation of security practices. Emerging attack vectors target software supply chains and development infrastructure directly.
Tomorrow’s DevSecOps will incorporate even more automated reasoning about security implications. Expect tools that not only detect vulnerabilities but suggest context-aware remediation strategies.
Getting Started: Your DevSecOps Action Plan
Immediate Impact Actions
Begin with quick wins like implementing basic SAST scanning in your CI pipeline. These initial steps demonstrate value while building momentum for broader adoption.
Conduct a dependency analysis to identify vulnerable components in your applications. This often reveals immediate security improvements with minimal development effort.
Initiate security champions recruitment from interested developers. Their enthusiasm will help drive cultural change from within development teams.
Building Long-Term Success
Create a phased DevSecOps roadmap tailored to your organization’s specific needs and maturity level. Set realistic milestones that deliver incremental security improvements.
Measure your progress using concrete metrics like reduction in production vulnerabilities or decreased time to remediation. These data points help justify continued investment.
Connect with DevSecOps communities for shared knowledge and support. Organizations like OWASP and the DevSecOps community offer valuable resources for practitioners at all levels.
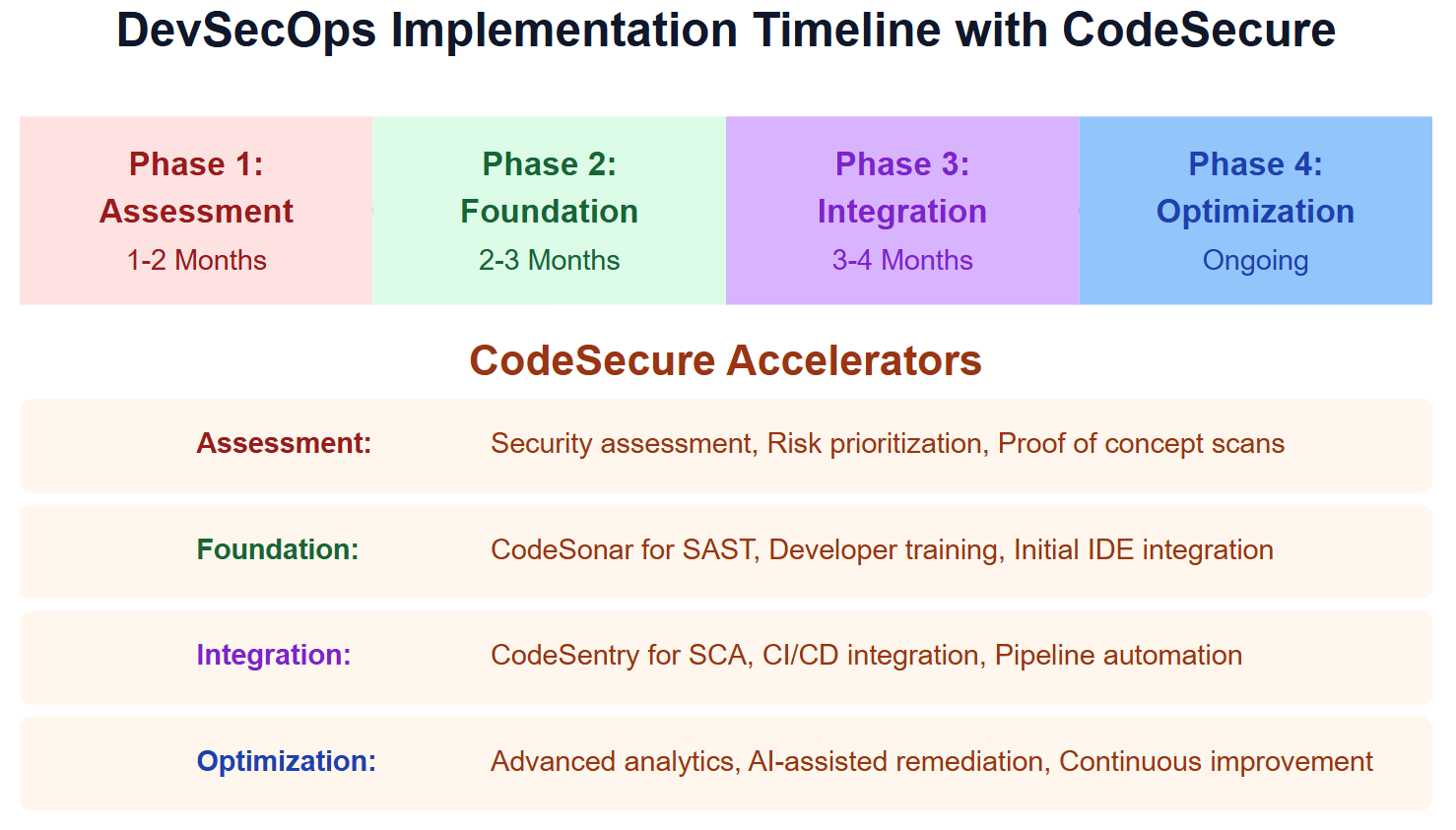
Experience the CodeSecure Difference
Request a demo of CodeSecure’s products to see how it can accelerate your DevSecOps transformation. Their security experts will help you identify the most impactful starting points for your organization.
CodeSecure’s implementation consultants provide guidance tailored to your industry and compliance requirements. Their expertise helps you avoid common pitfalls during adoption.
Join the growing community of organizations that have strengthened their security posture with CodeSecure. Their proven approach delivers measurable security improvements while supporting development velocity.
By implementing these DevSecOps practices with the right tools and support, your organization can build security directly into your development processes, reducing risk while increasing delivery speed. The journey requires commitment, but the resulting security improvements and efficiency gains make it well worth the investment.
download pdf